Businesses in the UK are subject to a continuous bombardment of cyberattacks. Opportunistic criminals are continuously searching for organisations that do not have the Cyber Essentials in place, regardless of their size. This is why 1 in 3 UK businesses report some kind of attack or breach per year, and half of those find it impacted their business operations somehow. [1]
From what we read in the news and see in the movies, we might imagine cybercriminals are hackers in hoodies with ninja skills or secretive nation-state cyber armies. This might lead us to think that our company is not under much threat if we don’t have nation-state-level secrets or the control system for a nuclear bunker. However, this isn’t the case.
Who are the hackers?
There is a complex interconnected web of organised cyber criminals trading in personal data and access to servers and botnets. One crime gang may be running massive phishing campaigns to hoover up login credentials and selling these for a few dollars each. Other gangs might buy these up to run targeted Business Email Compromise attacks – following your business processes to fool you into diverting a payment to an attacker’s bank account.
Yet others might be scanning the internet for vulnerable servers, installing botnet malware and selling access for a couple of dollars per machine. Others rent these servers to run Denial of Service campaigns – where a week-long DDoS attack can be had for $500. [4]
The main takeaway from all of this is that you’re under attack whether you think you have interesting data or not. Your credentials, your servers and your customer’s personal data all have value – the question is just how much. If you’re an easy target, your data will be floating around on the black market, and your server may be breached – just for the $2 a botnet herder can get to add it to their network.
Attack methodologies
The most common cyberattacks are:
- Phishing, 83% [1]
- Use of stolen credentials or impersonation 27%
- Scanning and exploitation,
- Ransomware or malware 13%
While the proportion of companies affected by each of these varies depending on who you ask, these are invariably the top four most common ways businesses’ IT systems are breached.
Phishing
“Phishing emails try to convince users to click on links to dodgy websites or attachments, or to give sensitive information away (such as bank details). “
UK National Cyber Security Centre.
Phishing is seriously common. Many people will receive phishing emails every month, which can be extremely convincing, even to security professionals who deal with these every day. While most phishing emails go ignored, around 3.6% of users are still sucked in on a typical phishing campaign [3]. So it is no surprise that around 1 in 4 UK businesses suffer some kind of Phishing attack each year, and 1 in 3 GDPR notifications to the ICO are of this nature. [1,2]
No protection is 100%, and attackers can keep sending messages until something works – so a multi-layered approach is a must:
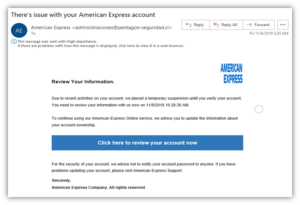 Prevent messages from reaching users:
Prevent messages from reaching users: - Email Filtering
- DMARC, SPF and DKIM anti-spoofing
- Help users spot and report fraudulent messages
- Security awareness training
- Ensure critical business processes are resistant to spoofing
- Protect your organisation from the effects:
- Use 2FA so that leaked passwords are not so useful
- Filter access to known malicious websites
- Detect and block malware
- Respond quickly to incidents
- Monitor your systems
- Have an incident response plan
Stolen Credentials
It can’t have escaped your notice that many websites and online services need you to sign up with an email address and password. Some of these do get breached from time to time. When this happens, the user databases, complete with thousands of email addresses and possibly passwords, get sold on the dark web. Now, a good website stores only a non-reversible “hash” of your password, which makes it easy to check if you supplied the correct password when you log in, but rather hard to turn the hash back into the original password. Nonetheless – many sites do not do this correctly.
If you want a sobering experience – visit https://haveibeenpwned.com/ and enter your email address. You’ll discover how many data breaches your email address has been found in. Now, think back – did you use the same password in any of those sites as you use now? If yes, people will try those credentials in anything they can find – corporate email servers, your LinkedIn account – that VPN you set up but haven’t used in ages. You get the idea.
What can you do about this?
- Don’t reuse passwords across multiple sites – use a password manager.
- Enable 2 Factor Authentication on anything of importance
- Monitor your systems
Scanning and exploitation
The internet is like the wild west – except on the internet, the Cowboys can knock on the door of everyone in the world in about 45 minutes.[5] This means that anything that is accessible from the general internet will receive a fairly continuous stream of attacks and probes for vulnerabilities. While you might think that keeping up with these threats is a hopeless task – the good news for defenders is that the internet has a lot of easy pickings.
According to IBM [6] threat intelligence report, 8 of the top 10 most exploited vulnerabilities in 2020 had been fixed by the software vendor over a year ago. This says that if you are prompt at installing updates, you can bat away most attacks.
Top defences:
- Firewalls – If it doesn’t need to be accessible from the internet, ensure it isn’t!
- Patching – Install updates to anything accessible from the internet promptly and at least within 14 days.
Ransomware
Ransomware features in about 1 in 5 cyber incidents. [2,6] In this attack type, the lucky recipient powers on their laptop to be greeted with a message stating that all of the data on their system has been encrypted. And, you can get the decryption key for an annoyingly plausible $80,000. And, for the less lucky, all their work colleagues also get the same message.
This can be more than an annoyance. Even if you have good backups – cleaning up after ransomware is time-consuming and requires careful attention to detail to avoid re-infection. An average company’s IT will be down for 23 days during the clean-up. Moreover, these days, ransomware gangs favour the double punch in the face of encrypting your data and threatening to publish it to the world if you don’t pay up.
For businesses of under 1000 employees, ransomware is most commonly delivered by the attacker logging on to an internet-facing server in your company via RDP using stolen or guessed credentials [6]. Most of the rest come through some type of phishing email to get credentials or directly deliver the ransomware software.
So your top defences are:
- Firewalls – Does your RDP server really need to be internet accessible?
- Anti-virus (on email and workstations)
- Two-factor authentication
- Backups
Conclusions
So you have all of the above covered. Is your data secure?
The above may cover the most common attacks and should be considered the “Essentials”. Your business’s specific risks depend very much upon what you do and the data you hold.
For each system or data “asset” you should think about:
- What would be the impact of this data being leaked to an outsider?
- What would happen if someone changed this?
- What is the impact if the system or data is lost, or temporarily not accessible?
You may also need to meet specific compliance or legal requirements – for example, if you hold payment card data, medical data, or personal information.
Furthermore – it is always wise to assume that you may be breached at some point and consider how you might find out (monitoring) and what you will do when that happens (incident response).
To leave you with one final thought – the ICO reports that more than half of breaches are from “non-cyber causes”, the most common of which is staff simply posting or emailing the wrong person.
While these are unlikely to be business-crippling events, there is more to Information Security than hacking.
REFERENCES
[1] DCMS Cyber Security Breaches survey 2021
[2] ICO Statistics
[3] Verizon 2020 DBIR
[4] Privacy Affairs Dark web pricing
[5] With a Gb internet connection, you can do a simple scan of every IP address on the entire internet in about 45 minutes!
[6] IBM X-Force 2021 Threat Intelligence Index







